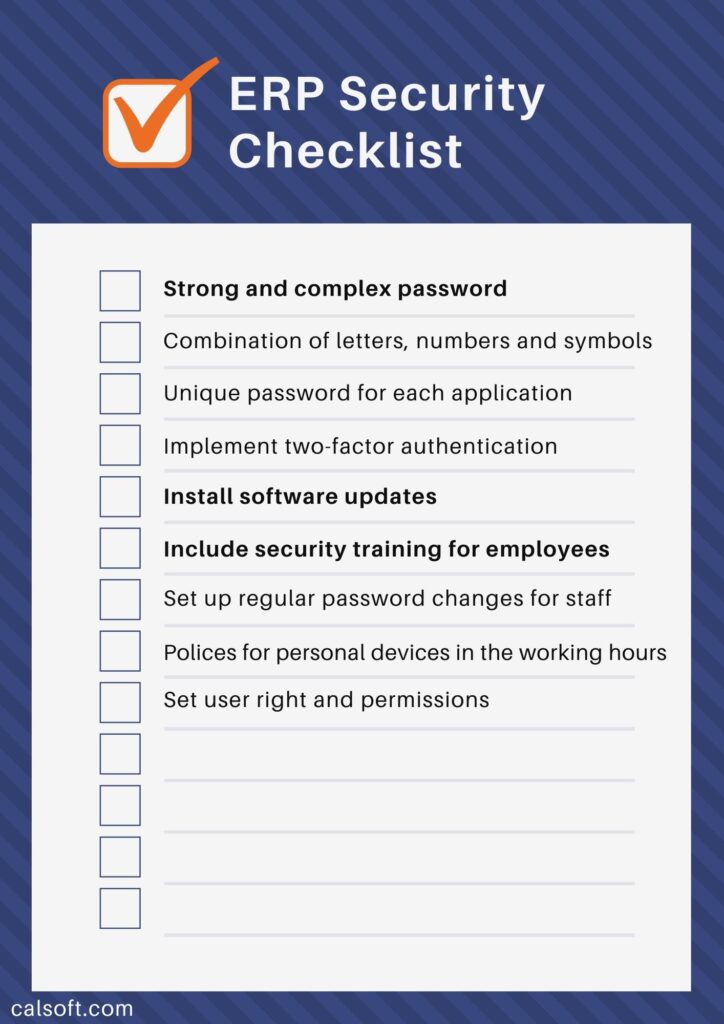
Data Security IT Complete Data Security Implementation Checklist | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

GDPR data protection and risk detection checklist infographic by Trustmarque - source large image and mor… | Cyber safety, Cyber security education, Data protection
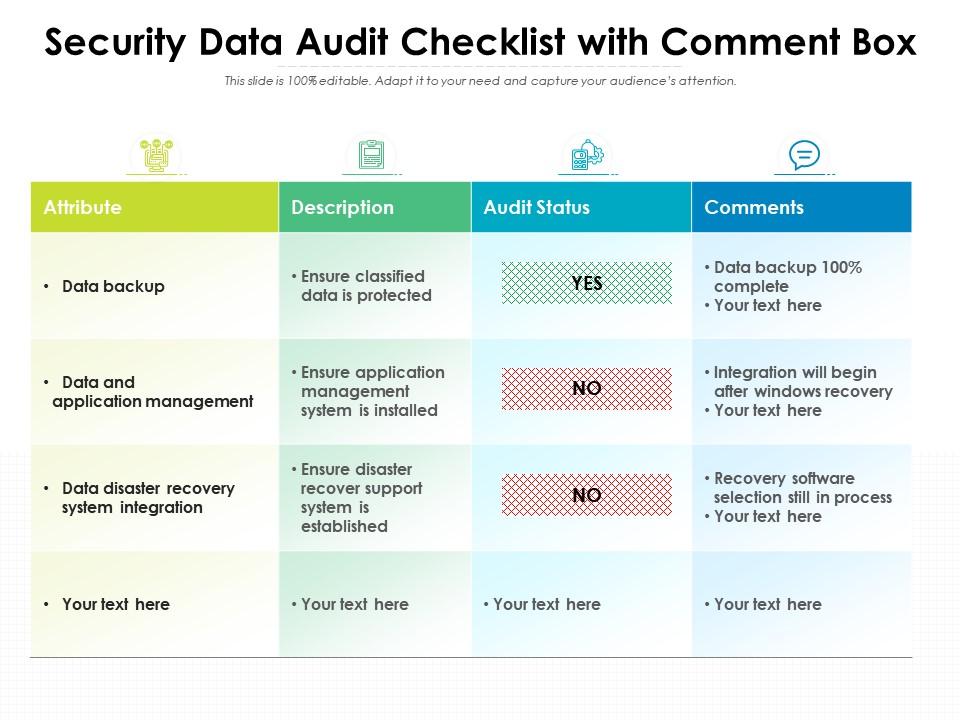

![The Sensible Small Business IT Security Checklist 2019 [Infographic] | iFeeltech The Sensible Small Business IT Security Checklist 2019 [Infographic] | iFeeltech](https://ifeeltech.com/wp-content/uploads/2017/12/THE-SENSIBLE-SMALL-BUSINESS-IT-CHECKLIST.png)
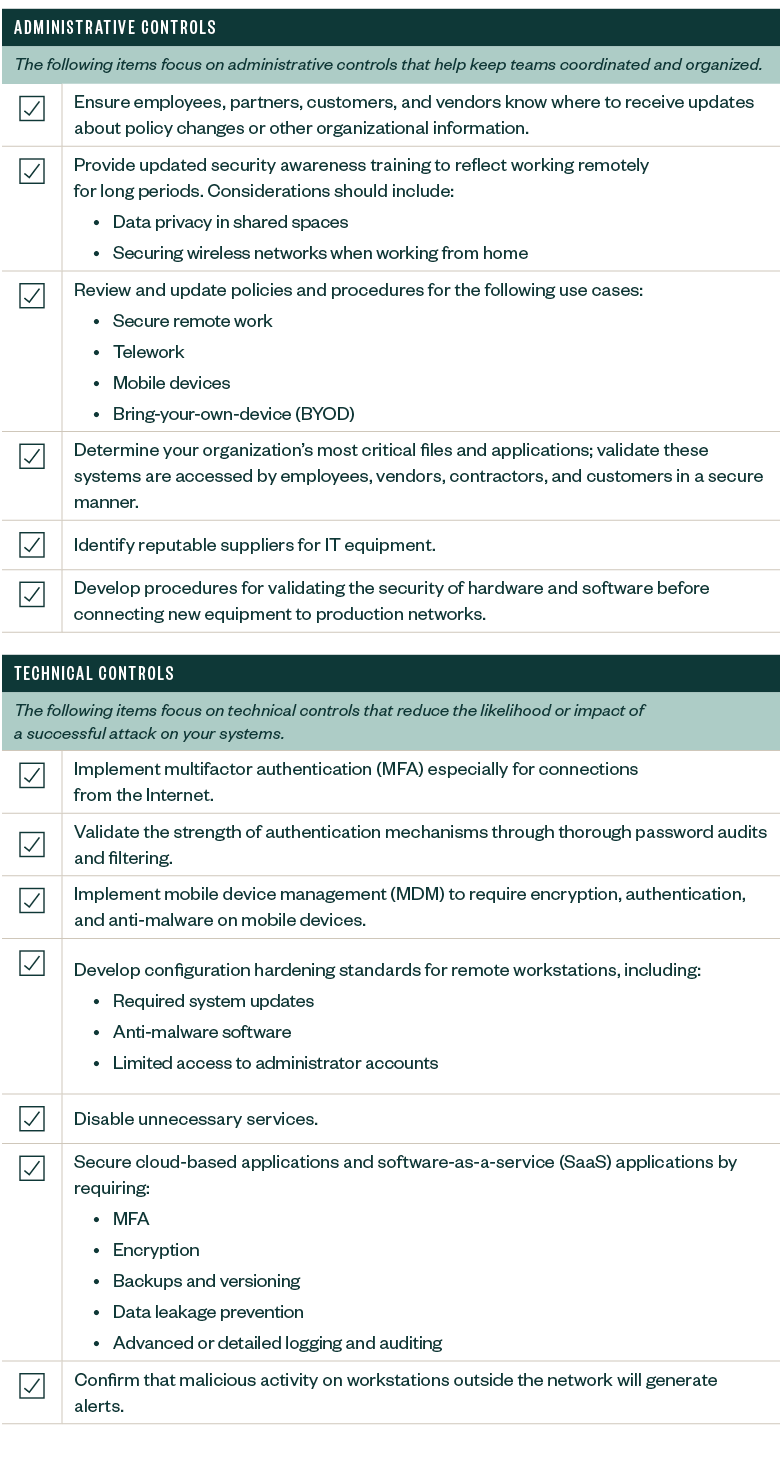







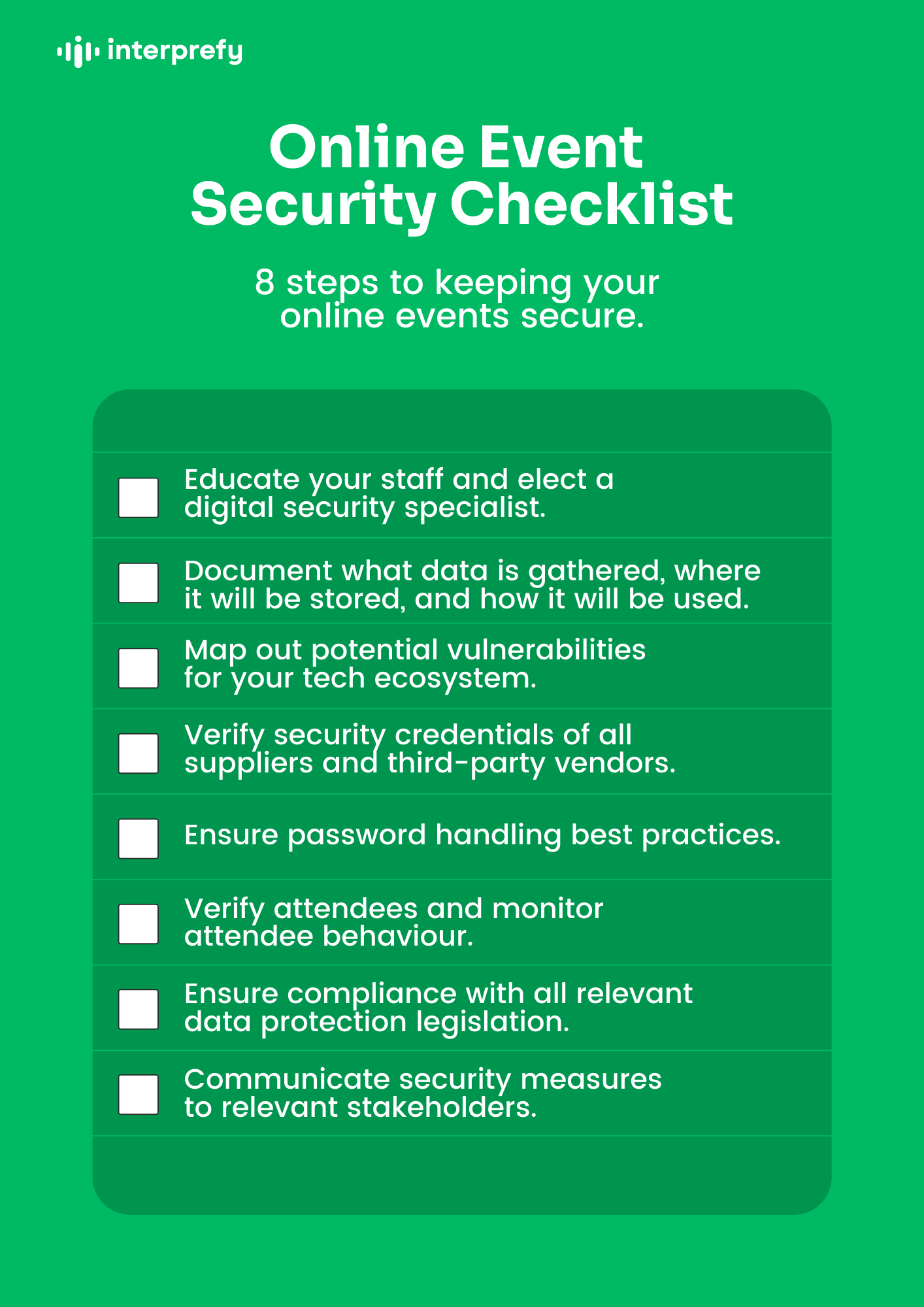
![Cyber Security Checklist [Infographic] - SecurityHQ Cyber Security Checklist [Infographic] - SecurityHQ](https://www.securityhq.com/wp-content/uploads/2022/08/SecurityHQ-Infographic-Cyber-Security-Checklist-531x1024.png)





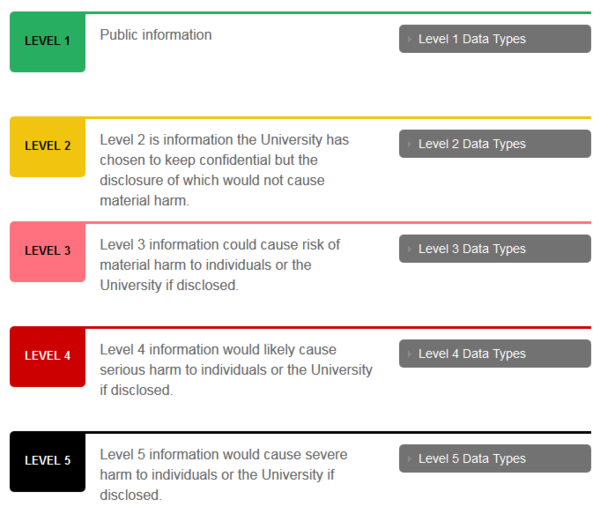

![Cybersecurity Checklist for E-Commerce Sites [Infographic] Cybersecurity Checklist for E-Commerce Sites [Infographic]](https://www.asiapremierbpo.com/wp-content/uploads/2021/10/Cybersecurity-Checklist-for-E-Commerce-Sites-v5-Infographic.jpg)