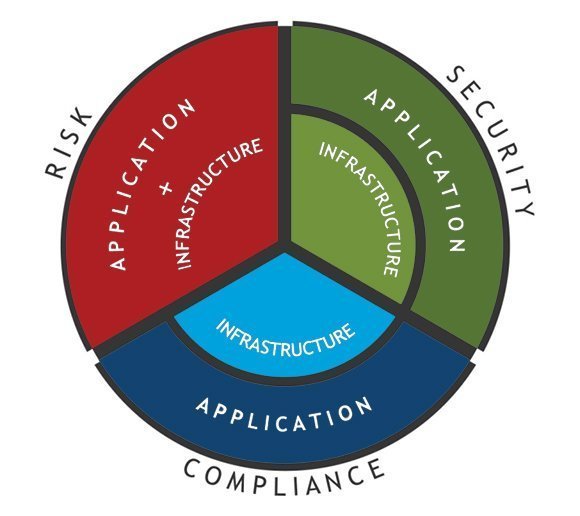
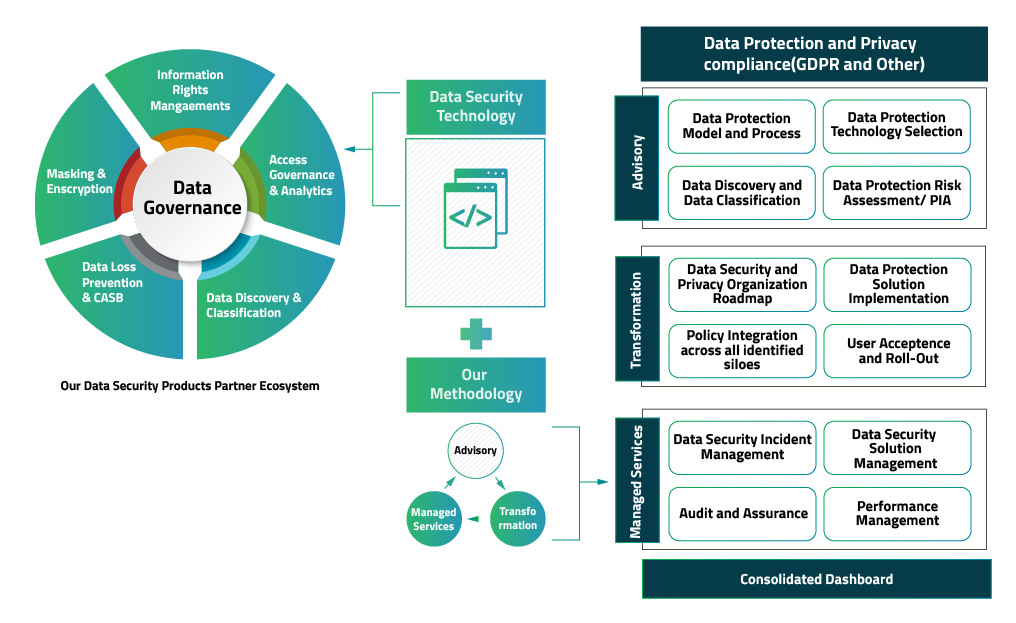
Compliance-driven Data Security - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Understanding the Data Security, Compliance and Customer Experience Trends Shaping Your Business in 2020 | Future of Sourcing