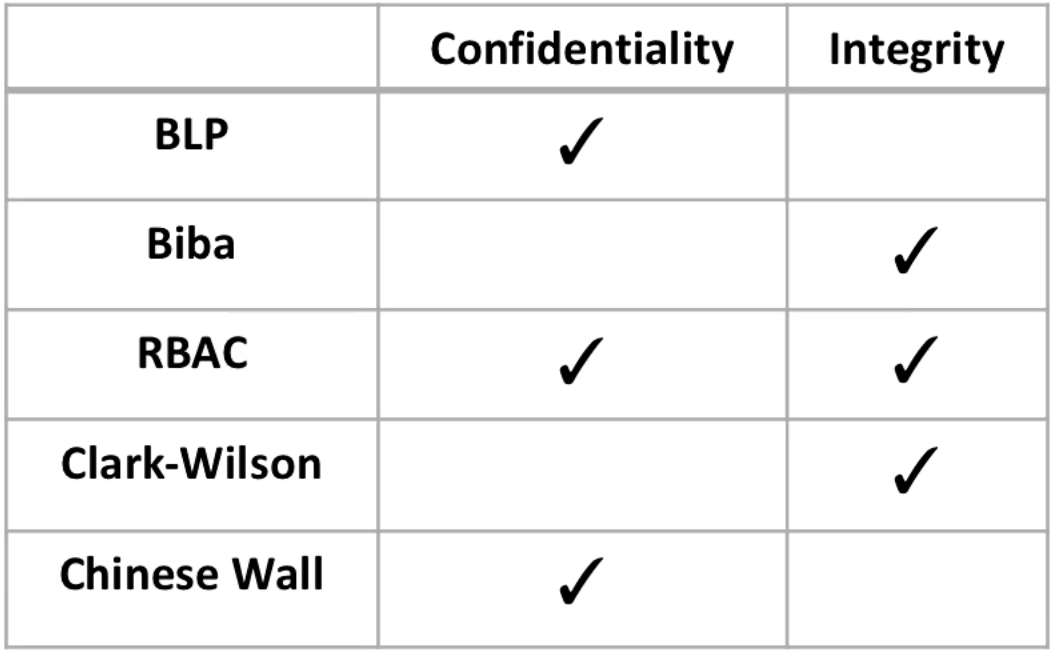
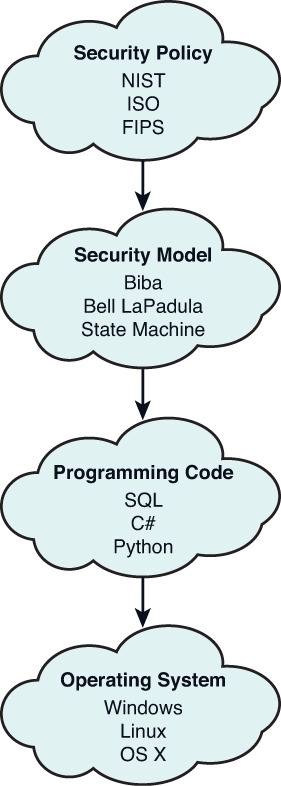
Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download

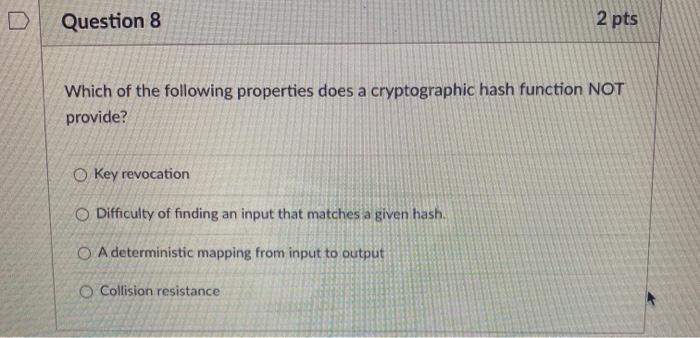
CISSP PRACTICE QUESTIONS – 20210401 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

CISSP PRACTICE QUESTIONS – 20210401 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Integrity Protection: Biba, Clark-Wilson, and Chinese Wall | CS 42600 | Study notes Computer Science | Docsity

Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram

Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download
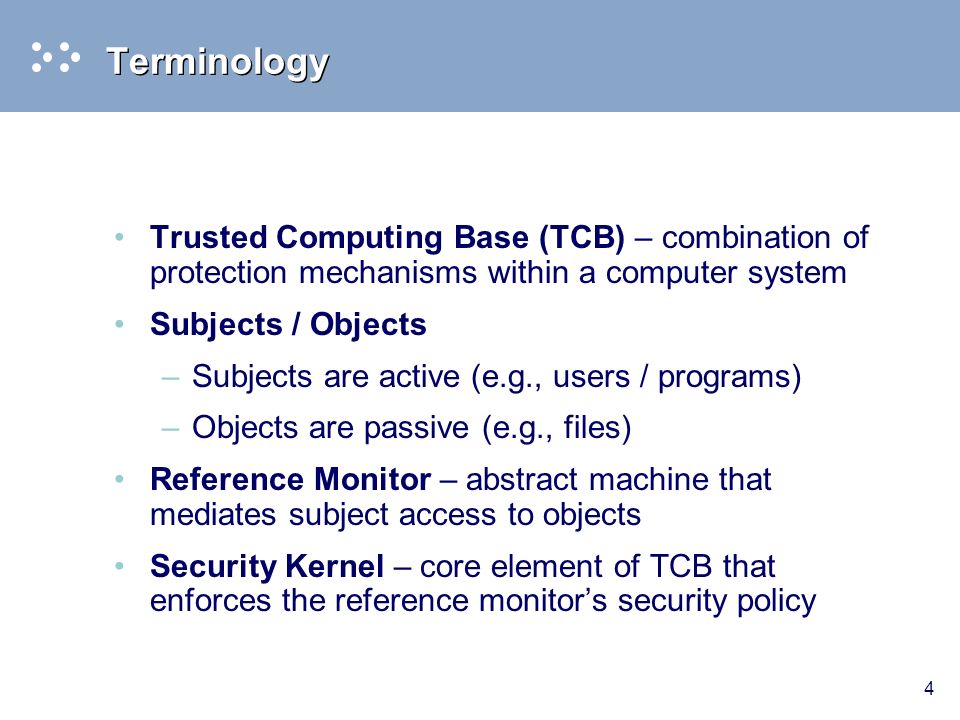
Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download